This is the first tutorial of a series that will culminate with a fresh WordPress site running on an Alibaba Cloud Instance.
In this tutorial, we will create and secure our instance running Ubuntu. Next we will complete a modern LEMP stack, with NGINX, MariaDB, and PHP7. Then we will run through Domain Management, adding DNS records, and installing a Let’s Encrypt SSL certificate, before finally moving onto installing WordPress via the CURL and WP-CLI. As an added bonus, there is a little extra on setting up a third party SMTP service for transactional emails.
While these tutorials are concerned primarily with configuring an Alibaba Cloud Instance, they should work just as well, with minor changes, for any Cloud VPS provider.
The reason I am using an Alibaba instance is that a client recently asked for a site to be hosted in China, and, for that, they provide the best solution with English language support. However while learning their infrastructure, it became quite clear that they provides a competitive addition to the Cloud Hosting market sector. If you want to experiment with their offering, they provide a $300 USD coupon to be used within 60 days of signing up for their service.
After signing up, and verifying my credit card, I was able to access their services via the Alibaba Cloud Console:
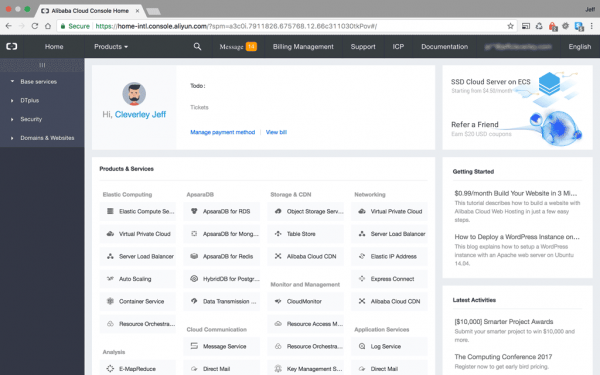
You’ll see the Elastic Compute Services (ECS) link in the top right of the main products and services panel, click that to move through to the ECS overview panel.
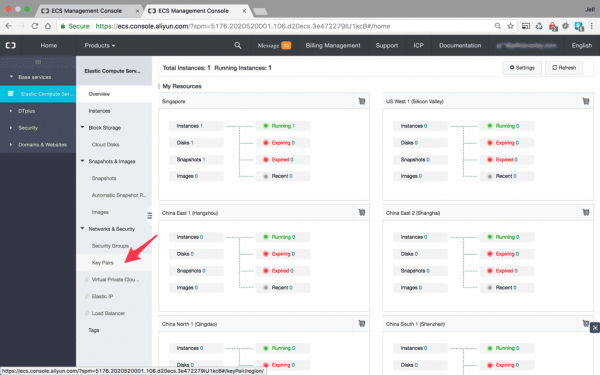
At this point, when I first provisioned a server, I rushed straight into ‘Instances’, a natural reaction I’m sure many will feel the urge to repeat, but hold your horses…
I advise you to go directly to ‘Key Pairs’, to upload your Public SSH key before you do anything else.
Why, you may ask? Well that’s because when you provision a server you should attach your public key, and if you haven’t uploaded one yet, it takes you out of the provisioning workflow and resets any previously selected choices.
So let’s do that first…
Wait, whats that you say? Some of you don’t have an SSH key? Okay then, I guess we’ll do that first then.
Step 1. Uploading your SSH Public Key
Open the terminal on your local machine, and enter the following command:
$ ssh-keygen
Assuming your local user were called “localuser”, you should see the following in your terminal:
Generating public/private rsa key pair. Enter file in which to save the key (/Users/localuser/.ssh/id_rsa):
This is the common path, so I suggest you just hit return to accept the file name and path.
You will also be prompted for a passphrase to secure the key with, this is optional, adding a password does add an extra layer of security, but it’s not necessary.
Now you will have generated a both a private key, id_rsa, and a public key, id_rsa.pub, in the .ssh directory of your localuser’s home directory.
These keys are needed to remote tunnel into your server, so don’t delete them. By default they are stored in a hidden folder, so they should be safe. On a mac you can always display your hidden folders using ⇧(shift) + ⌘(command) + .(period) .
Right then, now we can upload our public key in the ECS control panel. Just click on the menu link in the screenshot above, it’s on the left horizontal menu bar in the Network & Security section, and it will take you to the following settings screen:
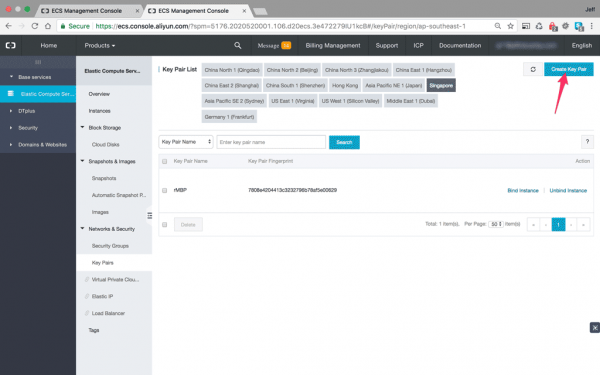
As you can see, I already have my public key uploaded, but you will need to the click the link in the top right to create a new key pair.
It will open a new settings panel below:
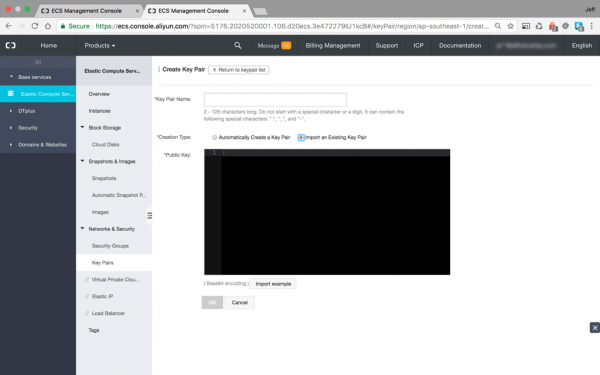
First, name your key pair, then select the ‘Import an Existing Key Pair’ radio button. A large black textarea entry box will open, into which you will copy and paste your public key.
Use the following command to print out your public id_rsa.pub key in the terminal of your local machine:
$ cat ~/.ssh/id_rsa.pub
Your public key should look something like this:
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQD0NlbKiLwqNHF/H+OcQd6ShGz34874837""";; sdkniwncnOYrwyUBqkBtulfZObTqh6vhbNxTChUbrIZpICE9wqTYVIvNDRc75bM2YEXBymYpZ4ZE17WwT +ko2UsxygWC+yxwG9pwvShHw/PCYxdE232n5l1hQe38VPDlEOBcti8ZRYO42XQxv0jcb86jbpbNoqO2yC fa/Aj6hJaSLcbGVdZRAijU/JCcKd7WTGIIhGWrw43q+HDLuF+9Z local_user@computer.local
Select all of this text and copy it to your clipboard, then paste it into the textarea box in the ECS key pairs settings panel from earlier.
Once complete, click OK and you will have created your key pairing, the key will be listed under your chosen key pair name in the key pairs settings screen, and will be available when you provision your Instance.
Step 2. Provision your EC2 Instance
Now we will create our ECS instance, head back to the instance Overview panel by following the link in the horizontal side menu. You will be greeted by the following screen:
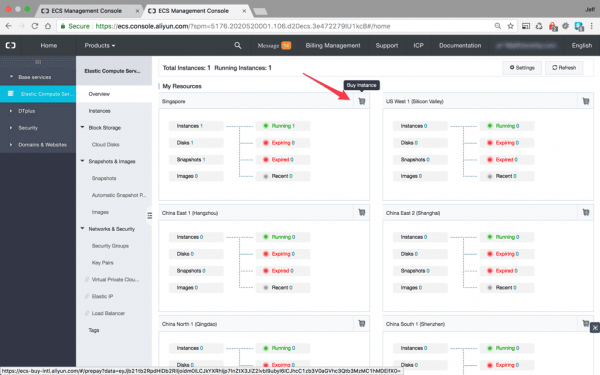
From the overview screen you can see all the locations where servers are available, and in the top right of each location pane there is a little checkout cart symbol link. Click that link.
A new window will open to create an instance, with all the configuration options, and a price bar along the bottom so you can see how configuration changes affect running costs on the fly.
In the ‘Advanced Purchase’ tab there are options for paying monthly by subscription, or by paying by the hour, while the ‘Starter Packages’ tab offers set configurations, which are available by subscription only:
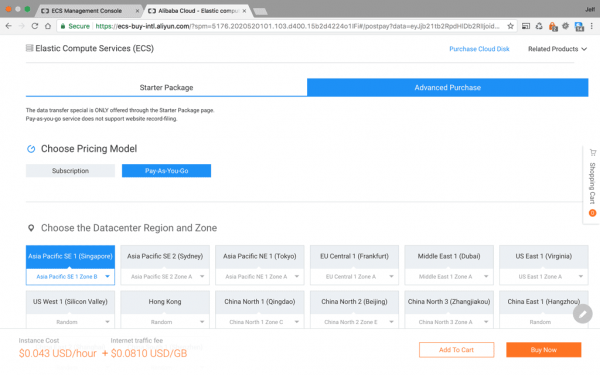
For this tutorial I selected ‘Pay-As-You-Go’ and the Singapore Datacenter, from the advanced tab The running cost is quite reasonable, but their cheapest starter package is USD $4.50 per month for a 1G server. That’s a big difference.
Or it would be, if we weren’t using their free credit.
Next we need to choose our Instance type and Network Type:
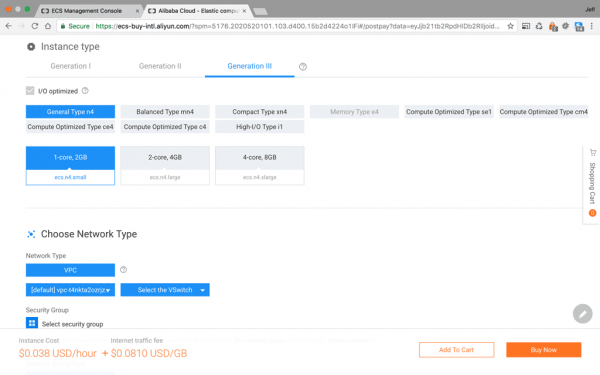
There are 3 generations of instance types, based upon different processor architectures, and in a twist, the latest generation instances are less expensive. I swapped my instance to a Generation III and the cost decreased marginally. Choose whichever configuration suits your needs.
You must also select network type, ‘VSwitch’, and Security Group. However in my experience, there is only one option for each of these in the advanced settings.
The security group is the Alibaba Cloud Firewall, there will only be a default option to select for now. We will be editing this later in the series to open ports for our Let’s Encrypt SSL.
Next up is the Data Transfer and Operating System configurations:
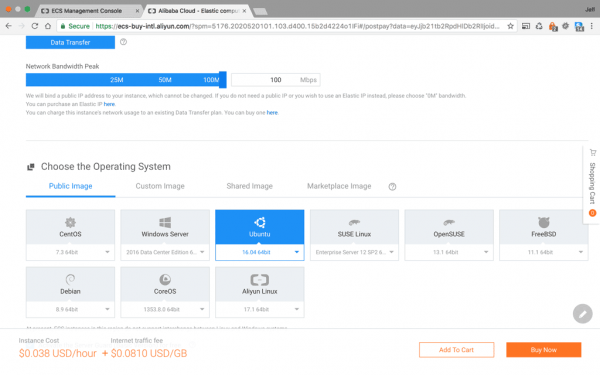
With advanced packages you are also charged by metered Data Transfer, you can set your Network Bandwidth to limit your exposure to higher costs. To be allocated a static IP address, you need to set your Network Bandwidth about 1Mbps.
After that you can choose from a wide range of operating systems and versions. For this series we will be using Ubuntu 16.04 64-bit.
Once these are configured, we move onto Storage and Security Settings:
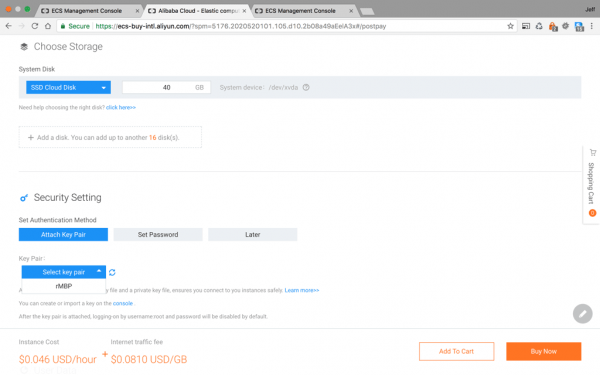
For storage they have an ‘Ultra Cloud Disk’ or an ‘SSD Cloud Disk’, I chose the fastest option the ‘SSD Cloud Disk’, which has increased the cost per hour by about 30%, but it’s on their dime so, gimme gimme gimme.
This is also where you attach your SSH Key Pair, if you created it earlier, as I suggested. If you didn’t and jumped ahead, then you’ll need to create it now, and restart this configuration process again afterwards. Bet you feel silly now eh?
Okay, nearly there, last but not least you will name your instance and check the overview:
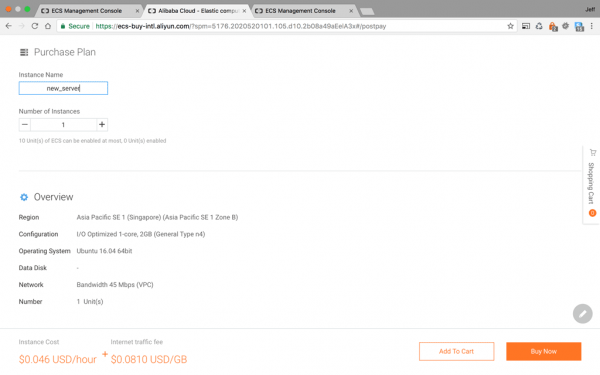
Choose your name, this will also be the Server’s hostname. Once you have checked the configuration Overview and are satisfied with your choice, click the ‘Buy Now’ button.
Before the instance is activated, you have to confirm your order:
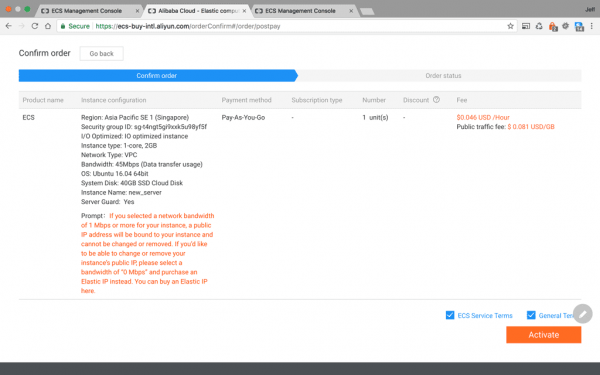
Click the ECS Service and General Terms and then you’re free to Activate your brand new instance.
If everything has gone according to plan you should be redirected to the Instances Console Panel, which lists all of your instances for each selected region, along with their IP addresses, general configurations, and links for management and reconfiguration:
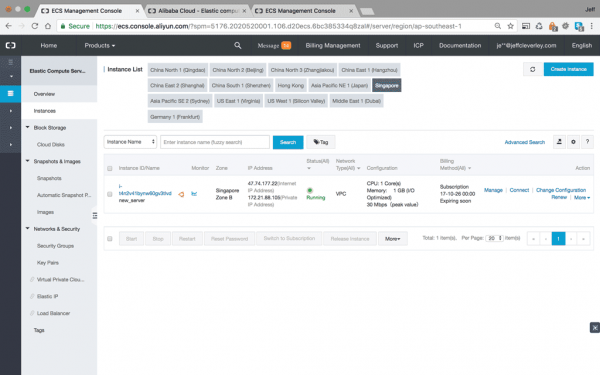
Step 3. Login as Root
If you are all done done admiring your shiny new Instance and investigating the various settings, it’s time to log in.
Copy your instance’s IP address, open your terminal and log in as root user using the following command, remembering to replace your_server_ip with the IP address you just copied:
$ ssh root@your_server_ip
Assuming you attached the Key Pair correctly during configuration, and you used the correct IP address, then the login process will include a warning about host authenticity, accept the warning and add the key to your known hosts, and your terminal should look like the following:
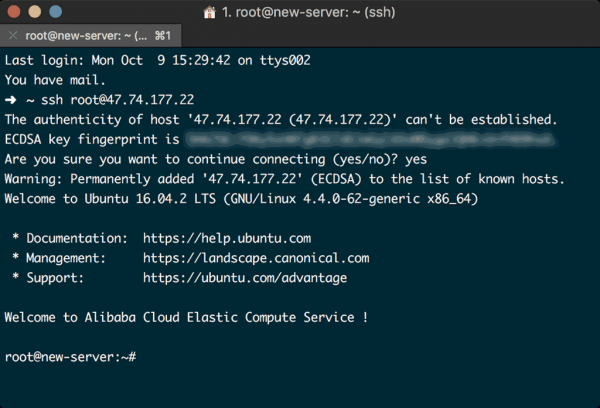
A few words about Root
In a Linux environment the Root user is the administrative user with a very broad range of escalated privileges. It is common practice to discourage the use of the root account on a daily/regular basis, primarily because this account has such heightened privileges that it’s very very easy to accidently cause havoc on your system, seemingly innocuous changes can be very destructive.
Step 4. Create a New Superuser
Given the inherent risks of using the root account, our plan is to create a superuser for everyday server managment. To do that we create a new user, and then add them to the Sudo group, this grants them the escalated sudo privileges required to make administrative changes on the system when necessary. The use of these sudo privileges will require a password entry from the superuser.
Once we have done this, we will disable remote root access to the server, helping securing it from ne’er-do-goods and other miscreants.
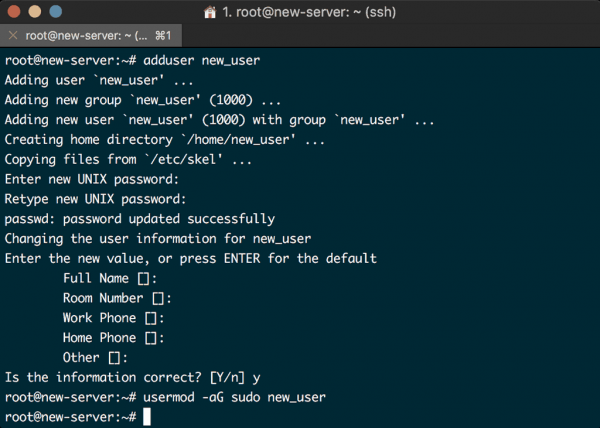
Create a new user with the following command. The new user I’ve created for this tutorial is called new_user, you should replace that name with one of your choosing:
# adduser new_user
You will be asked to provide a password, and add some user details. You should, of course, enter a strong password, but only fill in the additional details only if you like as they aren’t requisite, hitting ENTER in any field will just skip it.
Now you have a new user account with standard privileges, and since we want to disable root login later, we need to add this user to the sudo group to create the “superuser” with the necessary root privileges to do complete administrative tasks.
To do that issue the following command as root :
# usermod -aG sudo new_user
Your terminal screen should now look like this:
Step 5. Add Public Key Authentication to your Superuser
Remember the Public Key we added to our Alibaba account? That key is only available to the root user, therefore if we disabled root login now it would be impossible for our new_user to login.
That means we need to add that public key to a soon-to-be-created .ssh directory in our new_user‘s home directory.
First we need to switch to the new_user from root user by entering the following command:
$ su - new_user
Now we are in the new_user‘s home directory, located here in the full path /home/new_user/ .
Create a new directory called .ssh, and restrict its permissions, with the following command:
$ mkdir ~/.ssh $ chmod 700 ~/.ssh
Now, create and open a file in the .ssh directory called authorized_keys, using the built in nano text editor:
$ nano ~/.ssh/authorized_keys
Copy the same public key from earlier, id_rsa.pub, and paste it into the editor. Enter CTRL + X to exit the file, and y to save the changes, then ENTER to confirm the correct file name.
Once this is completed we need to restrict the permissions of the authorized_keys file, and return to the root user with the following commands:
$ chmod 600 ~/.ssh/authorized_keys $ exit
Step 6. Disable Password Authentication and Root Login
With your public key installed and accessible, your new_user will be able to login to the Instance directly. That means we can now further secure the server by disabling password-only authentication, and root login.
Doing this will restrict access to your server to Public Key Authentication only, meaning that the only way for someone to login to your server is if they possess the private key that pairs with the public key previously installed. In addition, disabling root login means that evern if someone did manage to get your private key, they would still be locked out unless they also knew your password.
If you have been following along exactly, you will be in the root account, if however you are still in your new superuser account, then just add sudo before each of the following commands.
Open the SSH daemon configuration file for editing:
# nano /etc/ssh/sshd_config
We are looking for 4 settings. We need to set PasswordAuthentication no, PermitRootLogin no, PubkeyAuthentication yes, and finally, ChallengeResponseAuthentication no.
Here are some screenshots from my system to show you the correct settings:
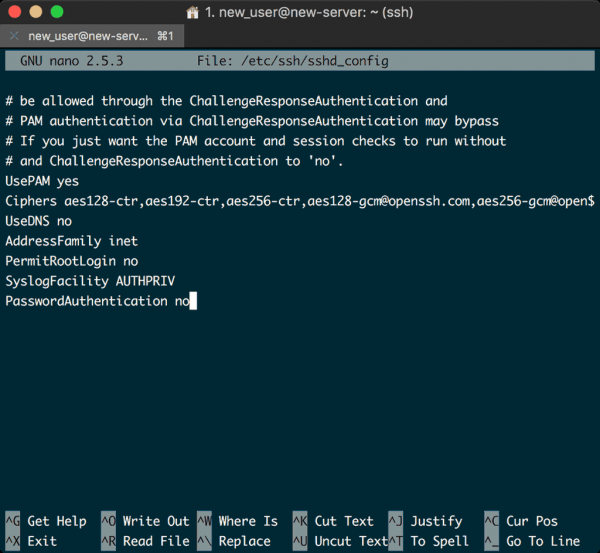
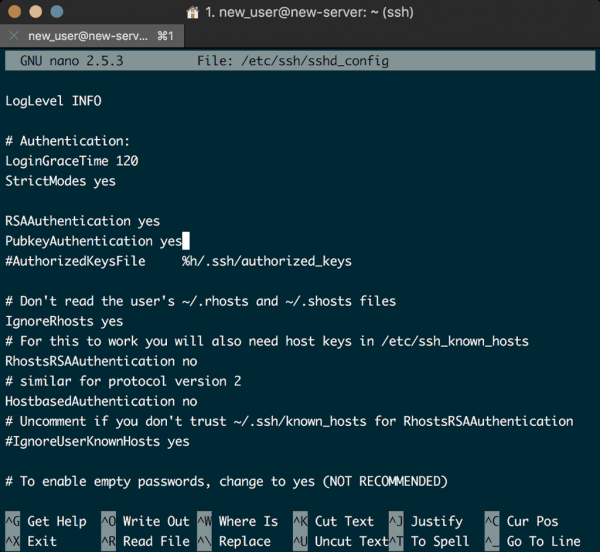
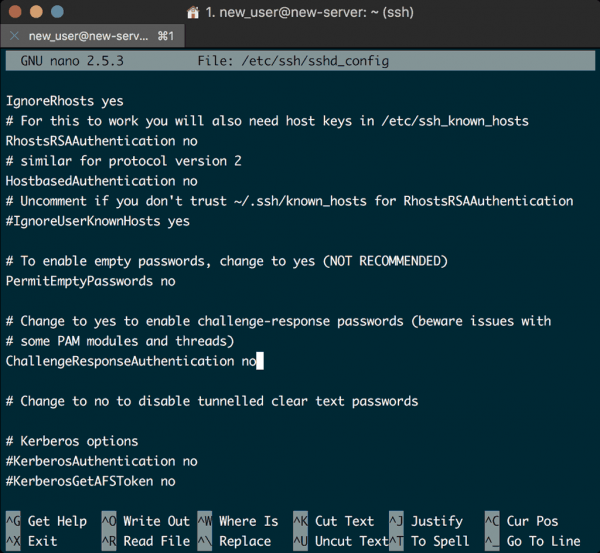
With those settings saved, your server should only be accessible by logging in with your superuser account.
Step 7. Test Superuser Login and Disabled Root Login
That being said, don’t go rushing and logging out of your server until we’ve confirmed everything is working as it should, otherwise our server will be inaccessible from the terminal, and would require resetting the root login from the Alibaba console.
Not that I am speaking from experience, of course not, not me… well not with Alibaba Cloud at least.
Open a new terminal on your local machine, and login to your server using the new account that you created. Remember to replace new_user and your_server_ip with your superuser and Instances’s IP address:
$ ssh new_user@your_server_ip
If all our configurations have been correct then you should see something like:
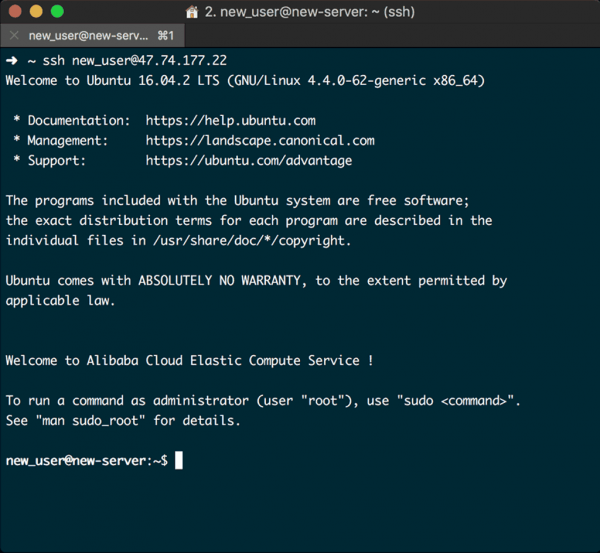
Well done, your superuser now has login access to your server via SSH public key authentication.
Just one more thing to test, we need to make sure that root login has been disabled. To do that, attempt to login as root using the following command:
$ ssh root@your_server_ip
I needn’t reminding you to replace your_server_ip with your Instances’s IP, need I?
All being well, I hope you see something like the following:
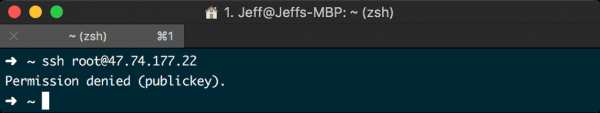
Step 8. Configure Ubuntu’s UFW firewall
The last thing we are going to do in this tutorial, is set up the simple firewall that comes with Ubuntu, aptly name UFW, the Uncomplicated Fire Wall.
It is both very easy to configure, and gives some level of protection from nefarious attacks.
Whenever applications are installed to Ubuntu they register their profiles with UFW, this allows the firewall to, very easily, manage the applications by name.
We need to configure UFW to allow SSH connections before we enable it, so we can still log in, otherwise there may be tears.
Since OpenSSH already has a profile registered with UFW you will be able to see it by typing the following command. And remember, now we are logged in as our superuser, we need to type sudo before each command that requires administrative privileges:
$ sudo ufw app list
Which should return:
Available applications: OpenSSH
To ensure SSH connections are allowed through the firewall we can instruct UFW by issuing the following:
$ sudo ufw allow OpenSSH
After doing this, we can safely enable the firewall by entering:
$ sudo ufw enable
It will issue a warning, and require you to type y and press ENTER. Once completed, you can verify that SSH connections are allowed through the UFW by issuing the following command:
$ sudo ufw status
The above combination of commands and outputs should result in a terminal that looks like the following:
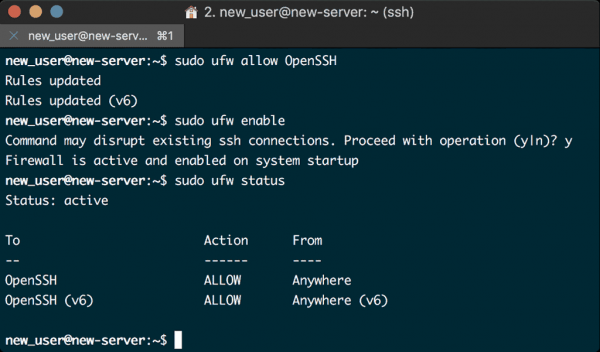
And that’s it.
We have now provisioned an Alibaba Cloud EC2 Instance with an Ubuntu 16.04 installation, and performed some of the necessary actions to secure it.
We now have a versatile foundation upon which to complete the LEMP stack, which we will do in the next tutorial.
See you then.
Jeff
Leave a Reply